Legions of law firms and legal service professionals have been well served by industry s original software programs. The Clearwell ediscovery Platform Delivering Intelligent ediscovery Clearwell has been instrumental in helping us manage our in-house ediscovery practice, saving NBC Universal valuable resources in people. IST ediscovery provides a full range of on-site litigation support and off-site ediscovery services that will take you from Early Case Assessment ECA through hosted. Linthicum Introduction Many new and existing business processes and information continue to move outside.
Nuix continues rapid growth, expands e-discovery into information governance Analyst: David Horrigan 8 Mar, Australian e-discovery vendor Nuix has embarked on a busy , releasing three new components. Request for Information No. November 14, Event Timeline: Email archiving, compliance, and ediscovery solution designed specifically for U.
Am I part of a Cloud First agency? The cloud applications questions. Archiving and ediscovery Introduction The data explosion that has burdened corporations and governments across the globe for the past decade has become increasingly expensive and difficult. Webconference The Radicati Group, Inc.
Copyright November , Reproduction Prohibited 9: June 5, Questions Deadline: Mimecast delivers a secure, dependable and highly scalable. Veritas AdvisorMail Email archiving, compliance, and ediscovery solution designed specifically for U. This Webcast Will Begin Shortly If you have any technical problems with the Webcast or the streaming audio, please contact us via email at: Is your practice drowning in paperwork? ImagIN Health Solutions is a set of software and services designed to help you. Place image here The Future of Information Management Bill Tolson Iron Mountain In the face of an ongoing electronic information explosion, information management becomes an imperative.
404 NOT FOUND
Me I am not an attorney I am a technology enthusiast I am paranoid I have trust issues I see the best intentions. Making and responding to electronic discovery requests By Martin Felsky and Peg Duncan One of the significant impacts of electronic discovery on litigation is the way in which it reconfigures the adversarial. Symantec to Acquire Clearwell Systems, Inc. May 19, 1 Forward-Looking Statements This presentation contains forward-looking statements within the meaning of U.
Datosphere Platform Product Brief No organization is immune to the explosive growth in the volume of electronically stored information ESI. The rapid growth of ESI is having a tangible impact upon organizations. IBM Unstructured Data Identification and Management Discover, recognize, and act on unstructured data in-place Highlights Identify data in place that is relevant for legal collections or regulatory retention. Where are we now? Service and Policy Management Analytics Cloud. That number doubles annually. Nuix bolsters its e-discovery team and continues its push to information governance Analyst: David Horrigan 5 Sep, Over the past months, many e-discovery vendors and thought leaders have jumped.
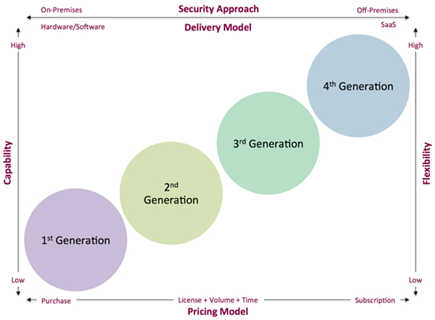
Moving to Office The Road to Microsoft Office Nov, http: From Hype to Reality Despite the enormous. Legal Technologies Considering Third Generation ediscovery? Start display at page:.
Related Video Shorts (0)
There's a problem loading this menu right now. Get fast, free shipping with Amazon Prime. Your recently viewed items and featured recommendations. View or edit your browsing history. Get to Know Us. English Choose a language for shopping. Not Enabled Word Wise: Not Enabled Screen Reader: Enabled Amazon Best Sellers Rank: Would you like to report this content as inappropriate? Do you believe that this item violates a copyright? Amazon Music Stream millions of songs. Amazon Drive Cloud storage from Amazon.
Alexa Actionable Analytics for the Web. AmazonGlobal Ship Orders Internationally. Amazon Inspire Digital Educational Resources.
Legal Technologies Considering Third Generation ediscovery? - PDF
Amazon Rapids Fun stories for kids on the go. The dark web is a component of the World Wide Web that is only accessible through special software or configurations, allowing users and website operators to remain anonymous or untraceable. The dark web forms a small part of the deep web, which is the part of the Web not indexed by web search engines.
The dark web has gained more notoriety over the past few years and several large criminal investigations have resulted in seizures of both cryptocurrencies and dark web pages and sites. Criminal enterprises involving counterfeiting, hacking, ID and IP theft, narcotics, child pornography, human trafficking, and even murder for hire seek a haven in the mist of encrypted communications and payment, such as Bitcoin, to facilitate their nefarious schemes.
While mining the dark web is critical for many law enforcement investigations, we are also seeing increased focus on this important evidence in civil litigation. Excellus Health Plan, Inc.
Product details
Fero arises out of a data breach involving healthcare provider Excellus Health Plan, Inc. The Plaintiffs brought a class action asserting claims under various federal and state laws. This evidence was summarized in an expert report providing the following conclusion: In other words, the dark web evidence was game-changing in this high-profile class action suit. Cases like Fero v. Excellus Health Plan illustrate that dark web evidence is essential for criminal and civil litigation matters alike.
Dark Web investigations do require specialized knowledge and tools to execute. For instance, X1 Social Discovery can be easily configured to conduct such dark web investigation and collections. Recently, Joe Church of Digital Shield led a very informative and instructive webinar on this topic. He included a detailed lesson on tools and techniques needed to search for and investigate key sources of evidence on the dark web.
This webinar is a must see for anyone who conducts or manages dark web investigations. Joe also featured a section on how to specifically utilize X1 Social Discovery to collect, search and authenticate dark web evidence. You can review this very informative 30 minute training session no sign in required by visiting here.
Time to reevaluate tools that rely on systemic data duplication. GDPR is applicable to any organization that provides goods and services to individuals located in the EU on a regular enough basis, or maintains electronic records of their employees who are EU residents. In additional to an overall framework of updated privacy policies and procedures, GDPR requires the ability to demonstrate and prove that personal data is being protected. As such, any GDPR compliance programs are ultimately hollow without consistent, operational execution and enforcement through an effective eDiscovery information governance platform.
However, some content management and archiving tool providers are repurposing their messaging with GDPR compliance. For example, an industry executive contact recently recounted a meeting with such a vendor, where their tool involved duplicating all of the emails and documents in the enterprise and then migrating all those copies to a central server cluster. That way, the tool could theoretically manage all the documents and emails centrally. Putting aside the difficulty of scaling up that process to manage and sync hundreds of terabytes of data in a medium-sized company and petabytes in a Fortune , this anecdote underscores a fundamental flaw in tools that require systemic data duplication in order to search and manage content.
- Primary Handbook for Timpani: A Beginning Method.
- The Interpretation of Murder: The Richard and Judy Bestseller.
- ?
- Subterraneum.
Under the GDPR, data needs to be minimized, not systematically duplicated en masse. It would be extremely difficult under such an architecture to sync up and remediate non-compliant documents and emails back at the original location. So at the end the day, this proposed solution would actually violate the GDPR by making duplicate copies of data sets that would inevitably include non-compliant information, without any real means to sync up remediation.
The same is true for the much of the traditional eDiscovery workflows, which require numerous steps involving data duplication at every turn. For instance, data collection is often accomplished through misapplied forensic tools that operate by a broadly collecting copies through over collection. And then the data is sent downstream for processing, which results in even more data duplication.
Load files are created for further transfers, which are also duplicated. Chad Jones of D4 explains on a recent webinar and in his follow-on blog post about how such manual and inefficient handoffs throughout the discovery process greatly increase risk as well as cost.
- Saint Martin la Tours Looking for Angels.
- Legal Technologies Considering Third Generation ediscovery?.
- !
- .
- ;
- ?
Like antiquated factories spewing tons of pollution, outdated eDiscovery processes spin out a lot of superfluous data duplication. In light of the above, when evaluating your compliance and eDiscovery software, organizations should keep in mind these five key requirements to keep in line with GDPR and good overall information governance:.
